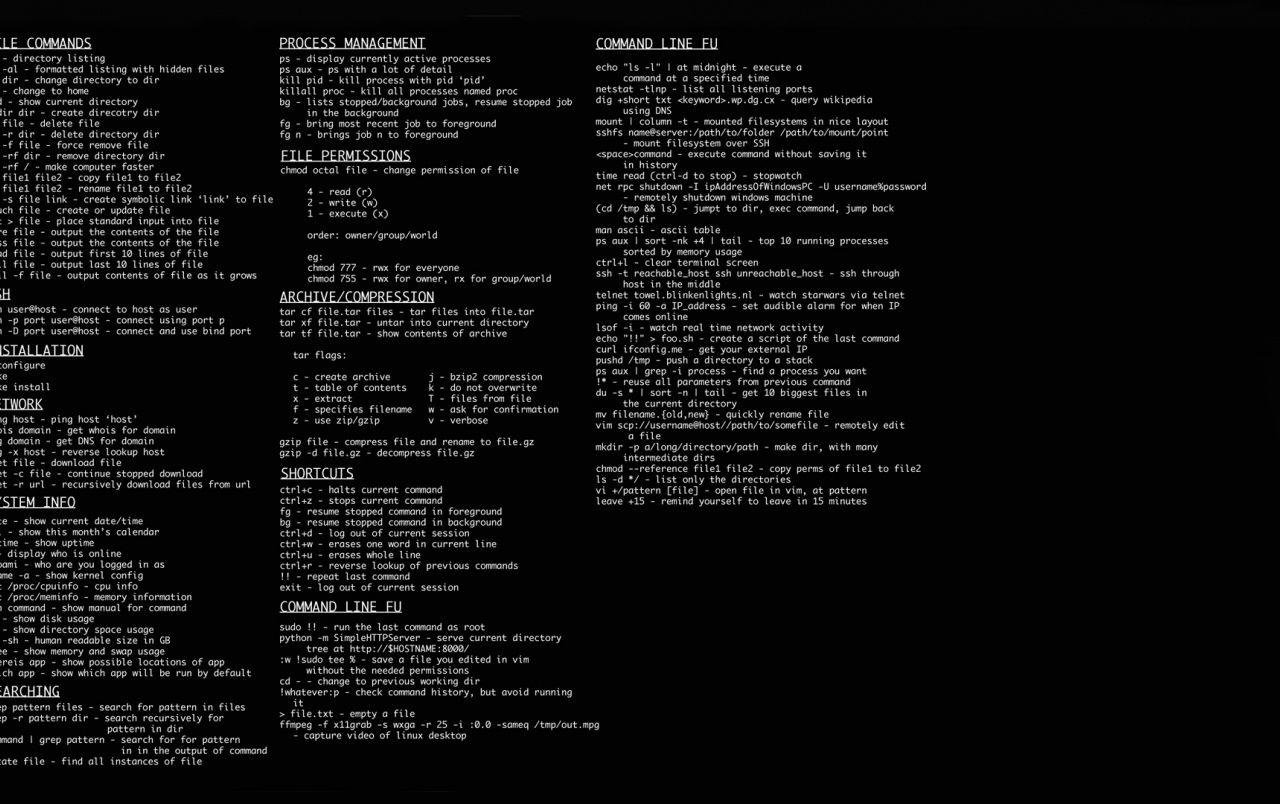
Assuming you would like a blog post titled “Airspace Cheat Sheet”: Have you ever looked up at the sky and wondered what all those different shapes and colors of airplanes meant? With this airspace cheat sheet, you will be able to understand the basics of airspace classification so the next time you gaze upon an airplane, you can have a better appreciation for where it is flying and why.
TOMATOFLAMES Memory Hack (So Freaking Easy!)
Most people think of the airspace as a three-dimensional space where airplanes fly. However, there is more to it than that. The airspace is actually divided into different classes, each with its own set of rules.
The National Airspace System (NAS) in the United States is divided into six classifications:
Class A: This is the busiest airspace in the country and includes airports like JFK in New York and LAX in Los Angeles. Only aircraft with instrument flight capability are allowed in Class A airspace.
Class B: This airspace surrounds major airports and has additional rules to help reduce congestion and ensure safety. All aircraft must be equipped with a transponder and maintain two-way radio communication with air traffic control at all times.
Class C: Similar to Class B airspace, Class C surrounds medium-sized airports and has additional rules to reduce congestion and ensure safety.
All aircraft must be equipped with a transponder and maintain two-way radio communication with air traffic control when entering or departing the area.
Air Traffic Control Cheat Sheet
Air traffic control (ATC) is a service provided by ground-based controllers who direct aircraft on and around the airport. The main purpose of ATC is to prevent collisions, give advice and information to pilots, and ensure the safe and efficient flow of air traffic.
There are three types of ATC facilities: tower, approach/departure control, and en route center.
Each has different responsibilities, but all work together to keep aircraft moving safely.
Tower: The tower controller is responsible for all aircraft movements within the vicinity of the airport. This includes takeoffs and landings, as well as taxiing on the ground.
Approach/Departure Control: The approach/departure controller works with the tower controller to manage arriving and departing flights. En Route Center: En route centers are located across the country and provide services to aircraft flying between airports.
Ground-based controllers use radar and other technology to track aircraft in their airspace.
They communicate with pilots using radios, giving them instructions on where to go and what altitude to maintain. In some cases, they may also use visual signals (such as light guns) to communicate with pilots.
ATC services are vital for safe air travel.
By working together, ground-based controllers and pilots can ensure that aircraft stay clear of each other and arrive at their destinations safely.

Credit: www.pinterest.com
What You Need to Enter Each Airspace?
In the United States, there are four main types of airspace: Class A, B, C and D. Each one has different requirements for entry, so it’s important to know which kind you’re entering before you take off.
Class A airspace is the most restrictive and requires a pilot to have an instrument rating in order to enter. This is because Class A airspace generally surrounds busy airports where there is a lot of air traffic.
To get an instrument rating, a pilot must undergo additional training and pass a written exam.
Class B airspace is also quite restricted and requires pilots to have a clearance from air traffic control (ATC) before entering. This clearance must be obtained prior to takeoff and can usually be done by radio communication with ATC.
Once cleared for entry, pilots must maintain two-way radio communication with ATC at all times while in Class B airspace.
Class C airspace is similar to Class B in that pilots need a clearance from ATC before entering. However, Class C airspace is not as densely populated with aircraft as Class B so the clearance requirements are not as strict.
Pilots must still maintain two-way radio communication with ATC while in Class C airspace but they may be able to obtain their clearance after takeoff if they are unable to do so prior to departure.
Class D airspace is the least restrictive of the four classes and does not require pilots to obtain a clearance from ATC before entering. However, two-way radio communication must be maintained with ATC while in Class D airspace.
What is the 5P Checklist Aviation?
The 5P checklist is an aviation mnemonic for the five principal points of piloting: power, pitch, props, people and place. It is used to help pilots remember the key aspects of flying an aircraft.
Power: The engine(s) of an aircraft produce the power that is necessary to fly.
Pitch: The pitch of an aircraft’s propeller(s) determines the amount of thrust that is produced.
Props: The propeller(s) of an aircraft provide the thrust that is needed to move the plane forward through the air.
People: The people on board an aircraft include the pilot, copilot, and any passengers.
Place: The place where an aircraft is flying (e.g., airport runway, airspace, etc.) can affect its performance.
Where is Airspace in the Far Aim?
The Far aim is the airspace above the United Kingdom and Ireland. It is also known as the London FIR (Flight Information Region). The boundary of the Far aim extends from latitudes 60°N to 51°N, and from longitudes 5°W to 12°E.
What Equipment is Required in Class A Airspace?
There are three main types of airspace in the United States: Class A, B, and C. Class A airspace is the most restrictive and is generally located around airports. To fly in Class A airspace, you must have an aircraft that is equipped with a transponder and two-way radio communications. You also need to file a flight plan with the FAA and get clearance from air traffic control.
Conclusion
In today’s aviation world, there are a lot of different types of airspace out there. It can be confusing trying to keep track of all the different rules and regulations for each one. This blog post will help simplify things by providing a cheat sheet for the most common types of airspace.
Class A: This is controlled airspace that typically extends from 18,000 feet MSL up to 60,000 feet MSL. All aircraft must be on an IFR flight plan and in radio contact with ATC in order to enter Class A airspace.
Class B: This is controlled airspace around major airports.
The base altitude starts at surface level and goes up to 10,000 feet MSL. Aircraft must have clearance from ATC before entering this airspace.
Class C: This is controlled airspace around medium-sized airports.
The base altitude starts at surface level and goes up to 4,000 feet MSL (although it can go higher in some cases). Like Class B airspace, aircraft must have clearance from ATC before entering this area.
Class D: This is controlled airspace around small airports.
The base altitude also starts at surface level, but only goes up to 2,500 feet MSL in most cases (again, it can be higher in some instances). As with the other classes of controlled airspace, aircraft must have clearance from ATC prior to entering Class D space.